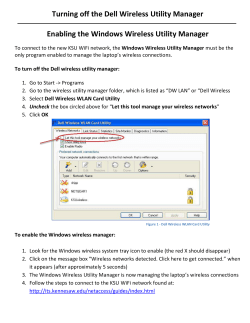
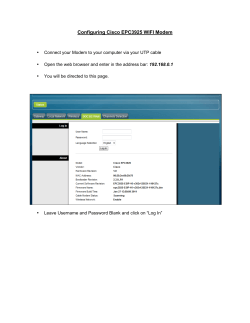
Banning Wireless Doesn’t Stop Users: Understand How to Protect Your Network
Banning Wireless Doesn’t Stop Users Aruba White Paper Banning Wireless Doesn’t Stop Users: Understand How to Protect Your Network and Support Wi-Fi Enthusiasts Banning Wireless Doesn’t Stop Users Aruba White Paper Table of Contents Introduction 3 Implementing “no wireless” 3 “No wireless” policies without enforcement don’t work 3 Progressing from “no-wireless” to secure wireless mobility 6 Provide secure guest access 6 Implement time-of-day or location restrictions 7 Limit users and devices to specific applications 7 Implement strict firewall enforced user policies 8 Conclusion 9 About Aruba Networks, Inc. 10 Aruba Networks, Inc. 2 Banning Wireless Doesn’t Stop Users Aruba White Paper Introduction Despite great strides in wireless LAN (WLAN) technology, many organizations continue to choose a “nowireless” policy, meaning wireless deployments of any kind are expressly prohibited by organizational guidelines. The basic goal is to eliminate any occurrence of wireless access, sanctioned or unsanctioned, within a defined space or location. The rationale for such a policy can vary, ranging from security concerns to a perception of operational complexity and prohibitive costs. However, in the quest to shut wireless out completely, two issues have arisen. First, many organizations do not consider the infrastructure requirements necessary to effectively enforce a “no wireless” policy. It is incorrect to assume that wireless threats will not exist simply because there is a “no wireless” policy and no ITimplemented wireless deployment. In fact, it is likely that wireless-related threats will always exist, regardless of the network design or internal mandates. Second, many organizations have become myopic in their quest for “no wireless.” These organizations may not realize that, as wireless equipment has matured, the options for deploying secure network mobility have expanded. The options are no longer limited to a binary decision of allowing or disallowing WLAN access. A range of controlled, restricted wireless policies that fall in between “open-wireless” and “no wireless” are now possible. Implementing “no wireless” Organizations have spent years and millions of dollars building moats around their computing infrastructure to protect it from the outside world. More recently, however, concerns have surfaced around internal threats, where legitimate users compromise the integrity of the network or gain access to privileged confidential data. Trusted individual clients are often the most overlooked aspect of network security. Add wireless to the equation and it can exacerbate this security hole unless a well thought out plan is in place. A simple laptop with an embedded wireless network interface card (NIC) connected to the organization’s infrastructure could expose intellectual capital in ways that a non-wireless client would not. Unauthorized access points also pose a threat, even when they are deployed in a non-malicious manner. “No wireless” policies without enforcement don’t work Though well intentioned, “no wireless” policies are often poorly implemented. In the worst case, organizations simply publish guidelines and prohibit IT from deploying WLAN equipment. The hope is that this will protect the organization from wireless-related attacks. Some organizations take a slightly more proactive approach, using periodic walk-through assessments that can report on malicious wireless activity. However, this method only offers a snapshot of the RF environment and is far from a comprehensive “no wireless” policy enforcement. Both approaches underestimate the wireless threats that can surface in a wired environment, even when wireless installments are “prohibited.” Organizations that take this tack will quickly realize the decision to implement a “no wireless” policy requires a full evaluation of associated security threats, clearly stated expectations of such a policy, and the infrastructure required to enforce it. These organizations will find that the only way to validate the absence of unauthorized WLANs and mitigate wireless threats is to deploy a best-in-class WLAN system which, at a minimum, must be able to perform the following functions: Aruba Networks, Inc. 3 Banning Wireless Doesn’t Stop Users Aruba White Paper Prohibit rogue APs – The solution must prevent any employee from installing rouge Access Points (APs) within the confines of a protected organization. Whether a network is wireless-enabled or not, rogue APs are one of the greatest threats to network security today. One employee with a $50 access point from a home electronics store can single-handedly open up the entire security perimeter, allowing anyone with a laptop and a wireless card free access to the internal network. Installing a system to automatically locate and disable rogue APs is an essential part of any security strategy – especially for enterprises choosing not to deploy wireless at all. However, it is not enough to detect rouges. A complete solution must identify and disable rogue APs, both on “the wire” and “in the air,” so that no clients will be able to communicate through them. Network planners must be very careful when looking for systems to identify rogue APs. There are two varieties: those that classify and those that do not. Systems that classify are able to automatically determine if an AP seen over the air is actually connected to the network or not. The end result is 100% certainty that what is flagged as a rogue AP is a genuine threat to the network. Upon identifying a threat, an effective system must automatically disable the rogue AP, preventing any clients from associating with it. Finally, network planners should choose a system that provides location tracking and real-time graphical views so the rouge AP can be quickly found and removed from the network. Figure 1. Rogue location tracking Less sophisticated systems flag everything seen over the air as “rogue” and leave the rest of the work to the network staff. An IT administrator must then associate with each “rouge,” try to figure out what network it is attached to, try to locate it, determine if it is a “rouge,” and then manually tell the system to shut it down. With so much room for error, it is easy for an administrator to either miss a real security threat or erroneously shut down a neighbor’s AP. At the end of the day, this type of system is almost like having no system at all. Aruba Networks, Inc. 4 Banning Wireless Doesn’t Stop Users Aruba White Paper Prohibit ad-hoc 802.11 – The solution must prevent all ad-hoc 802.11-based WLAN networks from occurring within the confines of a protected organization. Ad-hoc networks–uncontrolled WLANs operating only between clients, with no AP in the middle—constitute another class of rogue. The greatest danger posed by ad-hoc networking is a computing device running in ad-hoc mode while simultaneously connected to a wired LAN. Such a client can easily be compromised as an unauthorized entry point into the wired network, jeopardizing the company’s protected resources. Ad-hoc networks are particularly dangerous because anyone can join them – there is no authentication required, and typically no encryption is used. In an enforced no-wireless network, ad-hoc-enabled clients must be actively detected and disabled. A system that offers comprehensive RF monitoring can perform these functions by actively disrupting ad-hoc clients, as well as any clients attempting to associate with them, with de-authentication frames. This ensures that even if a device enabled for ad-hoc networking is connected to the network, it is rendered harmless. In turn, the RF monitoring system should send an alert to the network administrator so ad-hoc networking can be disabled on the violating client. Prohibit client bridging – A solution must give administrators visibility into misconfigured clients that are connected to the wired Ethernet network and are bridging their wired interface to a wireless connection. When bridging is enabled between two interfaces on a client, that client effectively becomes a rogue AP. A client configured as a bridge can inadvertently bridge two internal networks creating a network loop. Worse, in a “no wireless” environment, a client bridging an outside wireless network to an internal wired network represents a security hole. Public Network Internal Network Bridge Windows XP Laptop Figure 2. Client bridging An effective solution must implement advanced RF security to automatically detect wireless bridges, notify network administrators of their existence, and identify the location of the offending client on a building map. Aruba Networks, Inc. 5 Banning Wireless Doesn’t Stop Users Aruba White Paper Avoid disrupting other networks – A solution must prevent clients within the protected RF space from connecting to other organizations’ access points without disabling the operation of the other organizations’ access points or clients. Access points and clients at neighboring companies and hotspots aren’t harmful, but clients within a “no wireless” environment should be prevented from connecting to them. This must be achieved without hindering the operation of the neighboring networks and devices. An effective solution should automatically classify neighboring APs as “interfering,” not “rogue, and prevent “no wireless” clients from associating with them. This function can be accomplished with a combination of location-based services, client registration, and the same type of disruption methods used to prevent clients from attaching to rogue APs. Progressing from “no-wireless” to secure wireless mobility Most organizations recognize the benefits of user mobility, including productivity gains and the cost savings of overlaying convergence applications such as voice on a WLAN infrastructure. Concerns associated with wireless access have ebbed as security advancements have progressed, and many now consider wireless access to be more secure than the wired LAN. Wireless equipment compatible with 802.11i and the related WPA (Wi-Fi Protected Access) and WPA2 certifications provides rock-solid security without complicating the user experience. Some wireless equipment even complies with the stringent requirements of the U.S. government’s FIPS standards. Deployment of a WLAN solution has been greatly simplified as well. Early wireless implementations used distributed “fat” access points that were excessively difficult to deploy and manage. Even early centralized deployments were complex, requiring substantial hardware and software upgrades, as well as cumbersome reconfiguration to the existing network infrastructure. Additionally, the existing VLAN structure had to be greatly extended to accommodate the WLAN, adding significant complexity. It’s now clear that the risk of destabilizing the core network infrastructure to deploy a new service far outweighs the advantages. Next-generation wireless solutions now available eliminate these issues. These WLAN solutions are deployed as a simple overlay on top of the existing network without requiring upgrades or reconfiguration. Now mobility can be easily added as a new service, much like an additional server, without requiring any knowledge of or changes to the network to accommodate it. Because the underpinnings of an enforceable, comprehensive “no wireless” policy must include core components of an advanced WLAN infrastructure, it is relatively simple to incrementally enable mobility. In most cases, it’s simply a matter of adding APs to provide coverage or repurposing APs that were dedicated to RF monitoring to also provide client access. As wireless security and deployment concerns are addressed, organizations are beginning take advantage of the benefits associated with wireless mobility. A few examples are provided below. Provide secure guest access The first step for many organizations is to deploy dedicated wireless guest access, effectively treating wireless as an untrusted network. Organizations are under increasing pressure to provide wireless guest access, enabling visitors to perform their jobs and gain instant access to timely business information. Wireless guest access can be easily configured to protect internal network resources and even provide auditing of guest activity. Aruba Networks, Inc. 6 Banning Wireless Doesn’t Stop Users Aruba White Paper The impact on security and manageability should be negligible in moving from “no-wireless” to wireless guest access only. A guest access solution should not compromise the security of the network in any way and should not place excessive burden on the IT staff. In order to achieve this, the solution must include the following: • Secure Web Access – Client devices must be blocked from all access until a web browser is opened and authentication credentials are entered. The exchange of authentication credentials can be secured using industry-standard SSL. Mandatory acceptance of custom usage policies and guidelines can be required as part of the authentication process. • Firewalled Traffic Separation – A fundamental weakness in early guest access implementations was the reliance on VLANs for separating users. VLANs have proven unreliable in keeping users isolated and fully protected from one another. User-based policy enforcement must be done with an integrated firewall for maximum security. • Role-based Guest Provisioning – A role-based guest provisioning system enables secure and simple provisioning of guest users through a web browser interface. A receptionist can use such an interface to easily add, delete and modify guest user accounts, configuring each with an expiration date and time. • Secure Tunnel Redirection – Some advanced WLAN solutions allow guest traffic to be redirected to an IPSec or GRE tunnel for transport to another device located outside the corporate firewall. Using secure tunnel redirection, guest traffic is completely prevented from traversing any portion of the internal network, blocking any attempts to use crafted packets or VLAN hopping attacks. • Non-Disruptive Deployment – The existing network should be considered a no-touch zone, allowing for rapid on-demand deployment. Wireless devices should securely communicate with each other over IP networks. No reconfiguration of closet switches, routers, VLANs, or ports is required if the right solution is chosen. • Reporting – The system should provide auditing and reporting of who is using the network, when it is being used, and how it is being used. • Limited usage – A wireless guest access solution should allow the organization to limit guest access by protocol, thus restricting the type of traffic a guest user can send or receive. Restrictions should be able to be configured based on TCP port range, UDP port range, service type (e.g., HTTPS), and other Layer 4 protocols beyond TCP/UDP. Implement time-of-day or location restrictions In many cases, organizations find that the next step from a “no wireless” policy is secure wireless access restricted by time of the day and location. One of the operational benefits of a wired network is that access is only granted as long as the building is physically open. Some WLAN solutions available today provide the equivalent benefit with configuration options to turn an AP or group of APs off during certain time periods (e.g., overnight). This limits exposure to the wireless network and ensures that IT staff is always present to address issues as they arise Centralized WLAN systems with integrated firewalls can provide additional granularity by limiting WLAN access to certain users based on both time of day and location. This can be useful in developing access tiers for different groups of users. Limit users and devices to specific applications Another incremental step forward from a “no wireless” policy is to restrict users or devices to specific applications. Wireless solutions that include stateful firewalls can implement rules to match protocol, IP address and applications such as FTP, SIP, etc. Once application flows have been identified by the firewall, standard firewall actions such as permit, drop, log, or reject can be applied. Aruba Networks, Inc. 7 Banning Wireless Doesn’t Stop Users Aruba White Paper A stateful firewall is especially useful in securing and optimizing Voice over IP over WLAN (VoWLAN) networks through stateful recognition of traffic flows (e.g., SIP, H.323). Based on IP address, protocol and application information in the control channel, the firewall can selectively open ports for calls. This capability can prevent VoIP traffic from becoming a backdoor mechanism to attack the internal network Rules on the stateful firewall can also provide bandwidth controls on per-role basis (e.g., guests can be limited to specific throughput levels) to provide Quality of Service and prevent VoIP traffic from being overrun by data. Application-based prioritization requires stateful inspection, and this capability is a crucial difference between competing wireless solutions. Another powerful feature of advanced WLAN systems with a stateful firewall is blacklisting, where the administrator can automatically blacklist – or block from all network access – any client that violates specific firewall rules. This is particularly useful when single-purpose devices, such as voice over IP handsets, are used. For example, if a voice handset is observed attempting to conduct database queries or file server browsing, it is likely that the device credentials have been compromised by an intruder. Automatic blacklisting immediately disconnects the device from the network and generates an alert message to the administrator. Implement strict firewall enforced user policies An identity-based wireless solution that integrates encryption, authentication and access control into a single device can offer all the benefits of advanced mobility with a security level comparable to a network that fully enforces no-wireless. Because wireless devices authenticate to the network, identity is learned. Because encryption from those wireless devices terminates centrally, the system can ensure that network traffic was not forged by an intruder or tampered with in transit. Finally, if access control is done through a firewall, policy can be tightly tied to the identity and role of the user rather than to an arbitrary parameter such as IP address. This means that even a malicious insider cannot alter a MAC or IP address to “become” someone else; access control decisions are made on the basis of user identity, not network address. Wired desktop Access Controller Wireless laptop Access Point Authentication Authorization Identification Encryption Figure 3. Centralized authentication, authorization and encryption Aruba Networks, Inc. 8 Banning Wireless Doesn’t Stop Users Aruba White Paper Traditional fixed networks can only apply access rights to ports or VLANs. Mobile users and devices, by definition, do not connect to the network through a fixed port. The network must therefore identify every user and device that joins the network. A centralized wireless solution with an integrated firewall has the ability to be identity-aware and make permit/ deny decisions based on the identity of the user or device Once the role of the user is determined, appropriate rules may be applied that control what that user or device is permitted to do on the network. Conclusion Many organizations will continue to choose a strict “no wireless” policy in their network. It is critical that these organizations conduct a full assessment of the risks associated with this decision. Even with a “no wireless” policy, an advanced next-generation WLAN infrastructure has become a mandatory requirement to detect and mitigate wireless attacks. Advanced WLAN solutions provide much greater security whether deploying “no wireless” or adding some level of mobility. The figure below shows the relative level of security between deploying a next-generation WLAN infrastructure that enforces “no wireless” policies (upper curve), and a deployment that fails to properly enforce a “no wireless” policy or implements mobility with a legacy WLAN solution (lower curve). The overlaid benefit curve shows how improved network functionality and well-implemented security can greatly increase user productivity. Figure 4. Balancing security against the benefits of wireless Technology advancements now make it simple for organizations to deploy the infrastructure necessary to initially enforce “no wireless” policies and then take incremental steps towards providing advanced mobility, all without compromising security or adding network complexity. The key here is that a next-generation WLAN solution is essential to maintain stronger security both when there is a “no wireless” policy and when advanced mobility is added to realize greater user productivity benefits. Aruba Networks, Inc. 9 Banning Wireless Doesn’t Stop Users Aruba White Paper About Aruba Networks, Inc. Aruba Networks is a leading provider of next-generation network access solutions for the mobile enterprise. The company’s Mobile Virtual Enterprise (MOVE) architecture unifies wired and wireless network infrastructures into one seamless access solution for corporate headquarters, mobile business professionals, remote workers and guests. This unified approach to access networks enables IT organizations and users to securely address the Bring Your Own Device (BYOD) phenomenon, dramatically improving productivity and lowering capital and operational costs. Listed on the NASDAQ and Russell 2000® Index, Aruba is based in Sunnyvale, California, and has operations throughout the Americas, Europe, Middle East, Africa and Asia Pacific regions. To learn more, visit Aruba at http://www.arubanetworks.com. For real-time news updates follow Aruba on Twitter and Facebook, and for the latest technical discussions on mobility and Aruba products visit Airheads Social at http://community. arubanetworks.com. www.arubanetworks.com 1344 Crossman Avenue. Sunnyvale, CA 94089 1-866-55-ARUBA | Tel. +1 408.227.4500 | Fax. +1 408.227.4550 | info@arubanetworks.com © 2013 Aruba Networks, Inc. Aruba Networks’ trademarks include AirWave®, Aruba Networks®, Aruba Wireless Networks®, the registered Aruba the Mobile Edge Company logo, Aruba Mobility Management System®, Mobile Edge Architecture®, People Move. Networks Must Follow®, RFProtect®, and Green Island®. All rights reserved. All other trademarks are the property of their respective owners. WP_BanningWLAN_01XX13
© Copyright 2025