Introduction to IT i. up-to-date ii. best
Downloaded from: http://www.bsccsit.com/
M. SC. CSIT, Entrance Model Question 2012
CDCSIT, TU
FM : 100/ PM: 35
Time: 2 Hrs
Introduction to IT
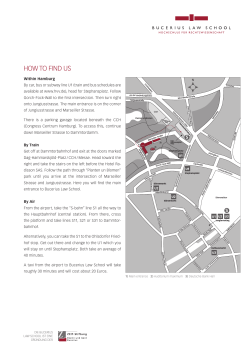
1. In computer technology, what is meant by the phrase 'state-of-the-art'?
i. up-to-date
ii. best
iii. latest
iv. all of the above
2. Which of the following is responsible for coordinating various operations using timing
signals?
i. arithmetic-logic unit
ii. control unit
iii. memory unit
iv. input/output unit
3. A new technology which provides the ability to create an artificial world and have people
interact with it is called ……………
i. televirtuality
ii. virtual reality
iii. alternative reality
iv. 3-D reality
4. Ergonomics is study of ……………………….
i. cost, relationship between computer hard-ware and software
ii. different computer operating systems
iii. gradation of various computer professionals
iv. human aspect of the environment around the computer system
C Programming
1. The use of break statement in a switch case is ……….
i. Optional
ii. Compulsory
iii. Gives error if not used
iv. None of the above
1
Downloaded from: http://www.bsccsit.com/
M. SC. CSIT, Entrance Model Question 2012
CDCSIT, TU
FM : 100/ PM: 35
Time: 2 Hrs
2. Name of the array contains …………………
i. value of first element
ii. address of first element
iii. starting address of whole block of the array
iv. both i & ii
3. Which of following requires post- testing of condition?
i. For loop
ii. Do- while loop
iii. While loop
iv. Whichever we use, it does not make any difference
4. Size of union is equal to ………………..
i. size of largest element in the union
ii. size of smallest element in the union
iii. sum of size all elements in the union
iv. none of above
Discrete Structures
1. Which of the following compound proposition is equivalent to p q?
i. p q
ii. q p
iii. p q
iv. Both b and c
2. Which of the following is not a linear homogeneous recurrence relation?
i. an = (1.11)an-1
ii. fn = fn-1 + fn-2
iii. an = nan-1
iv. an = an-5
2
Downloaded from: http://www.bsccsit.com/
M. SC. CSIT, Entrance Model Question 2012
CDCSIT, TU
FM : 100/ PM: 35
Time: 2 Hrs
3. Which of the following is the chromatic number of bipartite graph?
i. 1
ii. 2
iii. 3
iv. 4
4. Which of the following statement is true?
i. The value of maximal flow is equal to the value of minimal cut
ii. The value of minimal flow is equal to the value of maximal cut
iii. The value of maximal flow is equal to the value of maximal cut
iv. The value of minimal flow is equal to the value of minimal cut
Digital Logic
1. The decimal equivalent to (1101)2 is …………..
i. 12
ii. 13
iii. 24
iv. 25
2. Which of the following circuit maintains state information?
i. Sequential circuit
ii. Combinational circuit
iii. Multiplexer
iv. Decoder
3. The invalid state of an S-R latch occurs when
i. S=1, R=0
ii. S=0, R=1
iii. S=0,R=0
iv. S=1, R=1
3
Downloaded from: http://www.bsccsit.com/
M. SC. CSIT, Entrance Model Question 2012
CDCSIT, TU
FM : 100/ PM: 35
Time: 2 Hrs
4. The group of bits 10110101 is serially shifted (right-most bit first) into an 8-bit parallel
output shift register with an initial state of 11100100. After two clock pulses, the register
contains………..
i. 11110101
ii. 10110111
iii. 01111001
iv. 11010101
Microprocessor
1. Who invented the microprocessor?
i. Marcian E Huff
ii. Herman H Goldstein
iii. Joseph Jacquard
iv. All of above
2. What does microprocessor speed depends on?
i. Clock
ii. Data bus width
iii. Address bus width
iv. None of the above
3. For the 8085 assembly language program given below, the content of the accumulator
after the execution of the program is
3000 MVI A, 45H
3002 MOV B, A
3003 STC
3004 CMC
3005 RAR
3006 XRA B
i.
00H
ii.
45H
iii.
67H
iv.
E7H
4
Downloaded from: http://www.bsccsit.com/
M. SC. CSIT, Entrance Model Question 2012
CDCSIT, TU
FM : 100/ PM: 35
Time: 2 Hrs
4. The contents of accumulator before CMA instruction are A5H. Its content after
instruction execution is
i.
A5H
ii.
5AH
iii.
AAH
iv.
55H
Data Structure and Algorithm
1. Which of the following data structure is non-linear type?
i.
Strings
ii.
Lists
iii.
Stacks
iv.
None of above
2. When inorder traversing a tree resulted E A C K F H D B G; the preorder traversal would
return
i.
FAEKCDBHG
ii.
FAEKCDHGB
iii.
EAFKHDCBG
iv.
FEAKDCHBG
3. Which of the following is all pair shortest path algorithm?
i.
Dijkstra Algorithm
ii.
Directed Acyclic Graph
iii.
Floyd warshwall algorithm
iv.
All of the above
4. Given the following linked list, Which of the following correctly describes the steps to
delete element b from the above doubly linked list?
head
x
a
b
current
5
z
Downloaded from: http://www.bsccsit.com/
M. SC. CSIT, Entrance Model Question 2012
CDCSIT, TU
FM : 100/ PM: 35
Time: 2 Hrs
i.
curr.next.next.prev=Current.prev
curr.next = curr.next.next
ii.
curr.next = curr.prev.next
curr.next.next.prev=curr.prev
iii.
curr.next=curr.next.next
curr.next.next.prev=curr.next.prev
iv.
curr.next=current.next
head.next=Current.next.prev
Operating System
1. A program in execution is called ………..
i.
Process
ii.
Instruction
iii.
Procedure
iv.
Function
2. The scheduling in which CPU is allocated to the process with least CPU-burst time is
called …………………..
i. Priority Scheduling
ii. Shortest job first Scheduling
iii. Round Robin Scheduling
iv. Multilevel Queue Scheduling
3. Which of the following memory management technique is inefficient in terms of storage?
i. Bit map
ii. Linked list
iii. Tree
iv.
i & iii
4. To avoid race condition, the maximum number of processes that may be simultaneously
inside the critical section is ……………….
i. zero
ii. one
iii. two
iv.
more than two
6
Downloaded from: http://www.bsccsit.com/
M. SC. CSIT, Entrance Model Question 2012
CDCSIT, TU
FM : 100/ PM: 35
Time: 2 Hrs
Numerical Methods
1. The table below gives the values of tan x for 0.10<=x<=0.30:
x
y=tan x
0.10
0.1003
0.15
0.1511
0.20
0.2027
0.25
0.2553
0.30
0.3093
The approximate value of tan 0.12 using Newton’s interpolation is
i. 0.1397
ii. 0.1205
iii. 0.2689
iv. 0.1501
2. Which of the following is the ill conditioned system
i. 2x+y=2; 2x+1.01y=2.01
ii. 0.6x+0.6y=0.6; 0.4x+0.2y=0.5
iii. both i & ii
iv. none of above
3. Which one is the correct form of Trapezoidal Rule
xn
i.
ydx h 2y 0 2 y1 y2 .... yn 1 yn
x0
xn
ii.
y dx h 2 y
0
3 y1 y 2 .... y n 1 y n
0
4 y1 y 2 .... y n 1 y n
x0
xn
iii.
y dx h 2 y
x0
7
Downloaded from: http://www.bsccsit.com/
M. SC. CSIT, Entrance Model Question 2012
CDCSIT, TU
xn
iv.
y dx h 2 y
0
FM : 100/ PM: 35
Time: 2 Hrs
5 y1 y 2 .... y n1 y n
x0
4. Given the differential equation y”-xy’-y=0 with the conditions y’’(0)=1 and y’(0)=0,
using Taylor’s series method what is the value of y(0.1).
i. 1.0050125
ii. 1.2275125
iii. 1.0092345
iv. 1.4456981
Computer Architecture
1. Group of instruction that directs a computer is called …………..
i. Memory
ii. Logic
iii. Program
iv. All of the above
2. How many address lines are needed to address each memory locations in a 2048 x 4
memory chip?
i. 10
ii. 11
iii. 8
iv. 12
3. Memory access in RISC architecture is limited to instructions …………….
i. CALL & RET
ii. PUSH & POP
iii. STA & LDA
iv. MOV & JMP
4. When the RET instruction at the end of subroutine is executed,
i. the information where the stack is initialized is transferred to the stack
pointer
8
Downloaded from: http://www.bsccsit.com/
M. SC. CSIT, Entrance Model Question 2012
CDCSIT, TU
FM : 100/ PM: 35
Time: 2 Hrs
ii. the memory address of the RET instruction is transferred to the program
counter
iii. two data bytes stored in the top two locations of the stack are
transferred to the program counter
iv. two data bytes stored in the top two locations of the stack are transferred
to the stack pointer
Object Oriented Programming
1. Which of the following is not true about static data members?
i.
Static data members are instance variables
ii.
Memory for static data members is allocated only once
iii.
Memory for static data is allocated at the point of variable declaration
iv.
Static data members cannot be initialized inside the constructor
2. Constructors are executed automatically when
i.
Program execution starts
ii.
After object is created
iii.
Just before object is created
iv.
Just before program terminates
3. Which of the following is not needed in dynamic binding?
i.
Virtual function
ii.
Method overriding
iii.
Base class pointer
iv.
Method overloading
4. Main drawback of using inline function is
i.
It makes program execution slower due to extra overhead
ii.
It makes difficult to write programs
iii.
It makes size of object code large when there is large number of
calls to the function.
iv.
None of the above
9
Downloaded from: http://www.bsccsit.com/
M. SC. CSIT, Entrance Model Question 2012
CDCSIT, TU
FM : 100/ PM: 35
Time: 2 Hrs
Automata Theory
1. The regular expression over the binary alphabet for the string over {0, 1} that starts
with the same symbol is ……………………
i.
(0∑*0) U (1∑*1) U 0 U 1
ii.
(101∑*010) U (010∑*010)
iii.
(0∑*0) U (1∑*1)
iv.
11 U 00
2. Which is not true for Turing Machine?
i.
The head moves in both directions.
ii. The head reads as well as writes.
iii. Input string is surrounded by infinite number of blank in both sides.
iv.
Some symbols are pushed into the stack.
3. Unrestricted grammar is also known as ………………………………. grammar
i.
Type 0
ii.
Type 1
iii.
Type 2
iv.
Type 3
4. Given a grammar
S→ 0A0 | 1B1 | BB
A→C
B→S|A
C→S|ε
Which are nullable symbols in the grammar?
i.
A, B, C
ii.
A, B, C, S
iii.
C, S
iv.
C, B, S
10
Downloaded from: http://www.bsccsit.com/
M. SC. CSIT, Entrance Model Question 2012
CDCSIT, TU
FM : 100/ PM: 35
Time: 2 Hrs
System Analysis and Design
1. The tool used for process modeling is ………………..
i. Data flow diagram
ii. ER diagram
iii. Program flowchart
iv. Process diagram
2. An entity that borrows its primary key from another is known as ………………
i. Cardinal Entity
ii. Recursive Entity
iii. Weak Entity
iv. Strong Entity
3. …………… are the special tasks that signify the completion of major deliverables during
a project.
i. Deliverables
ii. Milestones
iii. Checkpoints
iv. Presentations
4. During the maintenance phase ……………….
i. System requirements are established
ii. System analysis is done
iii. Programs are tested
iv. None of the above
Computer Graphics
1. The equation of scaling transformation will be ......................
i.
X1=x+Tx, y1=y+Ty, z1=z+Tz
ii.
X1=x.sx, y1=y.sy, z1=z.sz
iii.
Both of these
iv.
None of these
11
Downloaded from: http://www.bsccsit.com/
M. SC. CSIT, Entrance Model Question 2012
CDCSIT, TU
FM : 100/ PM: 35
Time: 2 Hrs
2. Bresanham circle algorithm uses the approach of ...................
i.
Midpoint
ii.
Point
iii.
Line
iv.
None of these
3. Sp-line curve can be either ......................
i.
Bezier sp line
4.
ii.
B sp line
iii.
Both a & b
iv.
None of these
The types of projection are .............................
i.
Parallel projection and perspective projection
ii.
Perpendicular and perspective projection
iii.
Parallel projection and Perpendicular projection
iv.
None of these
Database Management Systems
1. A DBMS query language is designed to:
i. support end users who use English-like commands.
ii. support in the development of complex applications software.
iii. specify the structure of a database.
iv. all of the above.
2. Data independence means
i. data is defined separately and not included in programs.
ii. programs are not dependent on the physical attributes of data.
iii. programs are not dependent on the logical attributes of data.
iv. both (B) and (C).
12
Downloaded from: http://www.bsccsit.com/
M. SC. CSIT, Entrance Model Question 2012
CDCSIT, TU
FM : 100/ PM: 35
Time: 2 Hrs
4. With regard to the expressive power of the formal relational query languages, which of the
following statements is true?
i. Relational algebra is more powerful than relational calculus
ii. Relational algebra has the same power as relational calculus.
iii. Relational algebra has the same power as safe relational calculus.
iv. None of the above
5. Which of the following scenarios may lead to an irrecoverable error in a database system?
i. A transaction writes a data item after it is read by an uncommitted transaction
ii. A transaction reads a data item after it is read by an uncommitted transaction
iii. A transaction reads a data item after it is written by a committed transaction
iv. A transaction reads a data item after it is written by an uncommitted
transaction
Artificial Intelligence
1. Frames consist of .....................................
i.
collection of slot and slot values
ii.
collection of nodes and arcs
iii.
collection of arrays
iv.
collection of stacks
2. A* is said to be optimal if ........................
i.
ii.
iii.
iv.
the heuristic used is admissible
it always terminaties with a solution
the search space is already given with a path
no heuristic is used
3. Given a bayesian network;
A
B
C
13
Downloaded from: http://www.bsccsit.com/
M. SC. CSIT, Entrance Model Question 2012
CDCSIT, TU
FM : 100/ PM: 35
Time: 2 Hrs
a. consider B and C are idependent (with out any information about value of A)
b. B and C are dependent
which of above statements are true?
i.
only a is true
ii.
a and b both are true
iii.
only b is true
iv.
niether a nor b is true
4. Recurrent ANN ........................
i.
have signals traveling in both directions by introducing loops in the
network.
ii.
allow signals to travel one way only; from input to output.
iii.
allow loops in network but signal travels in one direction only
iv.
none of above
Design and analysis of Algorithms
1. If recurrence relation of an algorithm is T(n) = 9T(n/3) + n2, then time complexity is
given by
i.
O(n2)
ii.
O(n2log2n)
iii.
O(n2log3n)
iv.
O(n3)
2. Consider the segments given below: What is the number of stars printed by the code
segment
for(k=1;k<=n;k++)
{
for(j=1;j<=k; j++; j=j+2)
{
Printf(“*”);
}
}
14
Downloaded from: http://www.bsccsit.com/
M. SC. CSIT, Entrance Model Question 2012
CDCSIT, TU
i.
O(n)
ii.
O(nlogn)
iii.
O(n2)
iv.
O(logn)
FM : 100/ PM: 35
Time: 2 Hrs
3. Fractional Knapsack problem can be solved optimally in efficient way by using
i.
Dynamic Programming
ii.
Greedy Approach
iii.
Divide and Conquer Approach
iv.
None of the above
4. Which of the following is false about NP complete problems?
i.
They are not solvable by deterministic machines
ii.
They are solvable in super polynomial time
iii.
Their solution can be verified in polynomial time
iv.
They belongs to NP hard class
Web Technologies
1. An Internet authoring language that allows designers to create customized tags, enabling
the definition, transmission, validation, and interpretation of data between applications
best describes: …………..
i.
HTTP
ii.
XSL
iii.
XML
iv.
HTML
2. The script written for onload( ) event runs when ………………
i.
a document loads
ii.
a database loads
iii.
a server loads
iv.
a division loads
15
Downloaded from: http://www.bsccsit.com/
M. SC. CSIT, Entrance Model Question 2012
CDCSIT, TU
FM : 100/ PM: 35
Time: 2 Hrs
3. Cookies typically hold ………………..
i.
purchase history and credit card information
ii.
personal information in websites
iii.
unique identifier for a site visitor which may be linked to a customer
iv.
all of above
4. A computer that is connected to the Internet and stores files written in HTML, which are
publicly available through an Internet connection best defines: …………
i.
Web server
ii.
Application Server
iii.
Intranet Server
iv.
Tired Server
Simulation and Modelling
1. Which of the following are advantages of simulation?
i.
Simulation allows "what-if?" type of questions
ii.
Simulation can usually be performed by hand or using a small calculator
iii.
iv.
Simulation does not interfere with the real-world system.
i & iii only
2. All of the following are various ways of generating random numbers except
i.
Table of random numbers
ii.
Fibonacci series
iii.
Computer-generated random numbers
iv.
Von Neumann midsquare method
3. The three types of mathematical simulation models are
i.
Operational gaming, Monte Carlo, systems simulation.
ii.
Monte Carlo, queuing, maintenance policy.
iii.
Monte Carlo, systems simulation, computer gaming.
iv.
System simulation, operational gaming, weather forecasting.
16
Downloaded from: http://www.bsccsit.com/
M. SC. CSIT, Entrance Model Question 2012
CDCSIT, TU
FM : 100/ PM: 35
Time: 2 Hrs
4. The first step in the Monte Carlo simulation process is to
i.
Set up probability distributions.
ii.
Generate random numbers.
iii.
Set up cumulative probability distributions.
iv.
Establish random number intervals.
Computer Network
1. Which of the following protocol is supported by application layer?
i. TCP
ii. UDP
iii. HTTP
iv. IP
2. Which of the following is a class B IP address?
i. 192.168.0.25
ii. 155.155.55.15
iii. 27.0.0.24
iv. 90.23.21.32
3. Which of the following subnet-mask is used if we divide a class C IP address into 8 subnets?
i. 255.255.255.0
ii. 255.255.255.128
iii. 255.255.255.292
iv. 255.255.255.224
4. Which of the following is a LAN technology?
i. ATM
ii. Frame Relay
iii. X.25
iv. Ethernet
17
Downloaded from: http://www.bsccsit.com/
M. SC. CSIT, Entrance Model Question 2012
CDCSIT, TU
FM : 100/ PM: 35
Time: 2 Hrs
Compiler Construction and Design
1. Consider the grammar,
A→By|yB
B→xCx
C→zA|ε
What is First(A)?
i. {y}
ii. {x, y, z}
iii. {y, z}
iv. {x, y}
2. …..…………… are the last phases of compiler design.
i. Optimization & Code execution
ii. Optimization & Code generation
iii. Semantic Analysis & Code generation
iv. Code generation and Debugging
3. An …………….. is one whose value at a node in parse tree is defined in terms of
attributes at the parent and/or siblings of that node.
i. inherited attribute
ii. synthesized attribute
iii. imported attribute
iv. evaluated attribute
4. A variable x is …………….. of a loop if every time it is incremented or decremented by
some constant.
i. constant variable
ii. induction variable
iii. dead variable
iv. increment variable
18
Downloaded from: http://www.bsccsit.com/
M. SC. CSIT, Entrance Model Question 2012
CDCSIT, TU
FM : 100/ PM: 35
Time: 2 Hrs
Calculus and Analytical Geometry
1
1. What is the value of improper integral
0
1
x
dx
i. -2
ii. 2
iii. 1/2
iv.
2. What type of sequences {1 / x}xz
i. monotonically increasing
ii. monotonically decreasing
iii. neither monotonically increasing nor decreasing
iv. none of above
3.
If the letus rectum of an ellipse is 5 and eccentricity is 2/3. find the value of a & b.
i. a=9/2, b=45/4
ii. a=4/9, b=27/4
iii. a=2/9, b=4/54
iv. none of above
4. The locus of a point of intersection of a pair of perpendicular tangents drawn to the
conic is called ………..
i. polar
ii. hyperbola
iii. director circle of conic
iv. equation of directrix
19
Downloaded from: http://www.bsccsit.com/
M. SC. CSIT, Entrance Model Question 2012
CDCSIT, TU
FM : 100/ PM: 35
Time: 2 Hrs
5. What will be the limit of vector function
r (t ) = (cos) i + (sin) j + t k when t →π/4
i.
2
i
2
+
2
j
2
+
k
ii.
1
i
2
+
1
j
2
+
k
iii.
2
i
2
+
2
j
2
+
k
4
4
4
iv. both i and ii
6. What is the area of Cardioid r=a(1+Cosθ)
i. πa2
ii.
a2
2
iii.
3 a 2
4
iv.
3 a 2
2
w
?
7. If w=x2+y-z+sint and x+y=t. What is the value of
x y,z
i. 2y+cos(x+y)
ii. 2z+cos(x+y)
iii. 2x+sin(x+y)
iv. 2x+cos(x+y)
20
Downloaded from: http://www.bsccsit.com/
M. SC. CSIT, Entrance Model Question 2012
CDCSIT, TU
FM : 100/ PM: 35
Time: 2 Hrs
8. What is the value of fxx fyy – f2xy is ………..
i.
fxy
fyy
ii.
fxx
fxy
iii.
fyy
fxy
fxx
fyx
fxy
fyy
fxx
fyx
iv. none of above
9. What is the solution of second order differential equation D2+PD+Qy=0 if the roots are
real and equal?
i. y=(C1+C2x)emx
ii. (C1 x +C2)emx
iii. y=(C1-C2x)emx
iv. (C1 x -C2)emx
10. What is the I.F. of linear differential equation of first order if P=logx
i. 1/x
ii. -1/x
iii. x
iv. 1/x2
Linear Algebra
1. When a set of simultaneous linear equations are consistent?
i. rank of row matrix is equal to rank of column matrix
ii. rank of the coefficient matrix is equal to rank of augmented matrix
iii. rank of augmented matrix is equal to rank of row matrix
iv. rank of augmented matrix is equal to rank of column matrix
21
Downloaded from: http://www.bsccsit.com/
M. SC. CSIT, Entrance Model Question 2012
CDCSIT, TU
FM : 100/ PM: 35
Time: 2 Hrs
2. If one vector ei is not multiple of another, what type of vectors are they?
i. equal vector
ii. linearly dependent
iii. linearly independent
iv. None of above
3. Let T: |R2→|R be the linear transformation for which T(1,2)=3 and T(0,3)=2, then what
is the value of T(5,3)?
i. 31/3
ii. 25
iii. -3/31
iv. 4
4. Under what condition the inverse of square matrix A exists?
i. |A| = 0
ii. |A| = -∞
iii. |A| = ∞
iv. |A| ≠0
5
2
, what is cofactor of A?
5. If A=
4 3
3 5
i.
2
4
ii.
3 4
5
2
5 3
iii.
4
2
2 5
iv.
3
4
22
Downloaded from: http://www.bsccsit.com/
M. SC. CSIT, Entrance Model Question 2012
CDCSIT, TU
FM : 100/ PM: 35
Time: 2 Hrs
6. If v=(3,7), u1=(1,2), u2=(0,1) and v=a1u1+a2u2 then what is the value of a1 and a2?
v.
a1=3, a2=1
vi.
a1=2, a2=4
vii.
a1=3, a2=-1
viii.
a1=1, a2=3
7. Let T: |R3→|R3 be the linear map defined by T (x, y, z)= (0, y, z), then what are the
values if dimKerT and dimImT ?
i. dimKerT = 3, dimImT=3
ii. dimKerT = 1, dimImT=3
iii. dimKerT = 1, dimImT=2
iv. None of above
λx
8. If f(x) = e , then what is λ called?
i. Eigen Space
ii. Eigen Values
iii. Eigen Vector
iv. Spectral Vector
9. If u = (2,1,2) and v=(1,4, λ) are orthogonal to each other then what is the value of λ?
i. 3
ii. -3
iii. 0
iv. 2/3
10. When do the set of vectors {u1, u2,………,un} in a real vector space v is said to be
orthogonal?
i. < ui, uj >=0 for i ≠ j
ii. < ui, uj >=0 for i = j
iii. < ui, uj >≠0 for i ≠ j
iv. None of above
23
© Copyright 2025